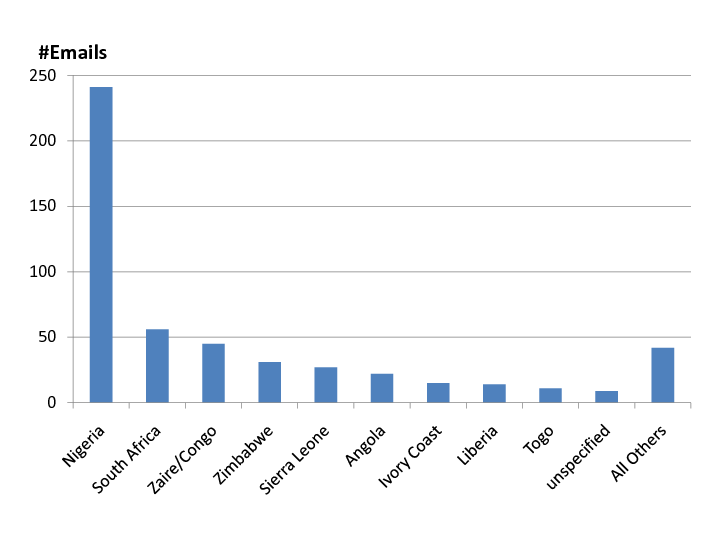
Country of Claimed Origin for 419 Emails, https://www.microsoft.com/en-us/research/wp-content/uploads/2016/02/WhyFromNigeria.pdf
This article is the first part of a two-part series on the recent upsurge in sextortion. Part 1 details the nature and scope of the threat, applicable criminal statutes, and background on the primary threat actor. Part 2 summarizes methods and tools being used to conduct sextortion-at-scale, victim traits targeted by cybercriminals, and protective/preventative measures.
No matter how tech-savvy teenagers or young adults may be or whether or not parents have discussed sextortion with them, awareness is not enough and families need to stay abreast of this growing threat. In 13% of National Center for Missing and Exploited Children (NCMEC) CyberTipline sextortion reports, the child victim had experienced some type of negative outcome. Of those reports with some type of negative outcome, it was indicated that about 1 in 3 children (31%; 4% of all sextortion reports) had engaged in self-harm, threatened suicide or attempted suicide as a result of the victimization (NCMEC, 2019). Cybercriminals’ mix of tools and techniques can change, as needed, so their capability inventory is almost limitless.
The Nature and Scope of the Threat
Sexual extortion, also known as sextortion, financial sextortion, porn scamming, or non-consensual pornography, is a form of digital/cyber extortion or online blackmail, a hybrid form of a romance scam, where a cybercriminal tricks or coerces victims into sending explicit sexual images or videos of themselves. The perpetrator then threatens to reveal the compromising material to the victim’s family, friends, and/or other associates if the victim does not provide more sexualized media content, pay the perpetrator and/or engage in some other act such as providing sexual favors. Sometimes the offender already possesses or claims to possess nude or sexual images of the victim and threatens to release them if the victim will not do as the offender instructs. The perpetrator may also threaten to harm the victim’s friends or relatives by using information they have obtained from their electronic devices unless they comply with their demands.
Sextortion is among the acts included in the definition of Technology-Facilitated Abuse (TFA) “an abusive or harmful…course of conduct facilitated through digital media (e.g., websites, social networking platforms, dating sites, apps, blogs, online games, instant messages, email) and targeted either directly or indirectly at a particular person or group of persons, often (but not always) with the intent to cause emotional distress, reputational damage, and/or fear for personal safety.” Other acts in TFA include cyberstalking, swatting, doxing, and nonconsensual pornography (RAND Corporation, 2020). Interestingly, Europol recommends the term “online sexual coercion and extortion of children” be used in lieu of sextortion to more accurately reflect the act.
Most parents have heard something about the Yahoo-boys of old — they are the original “Nigerian Princes” whose Nigerian letter and advanced fee (419) scams plagued victims for decades. Many parents may have received random spam emails themselves about malware on their computer or threats to release embarrassing personal details from compromised dating or other sensitive websites unless a cryptocurrency payment is made. Few parents connect this group or these emails to today’s exponential surge in sextortion cases.
The Internet security industry has been aware of the evolution of largely African-based threat actors for several years. As early as 2008, the rise of the Yahoo-boys sub-culture was linked with the emergence of the Internet which significantly altered the modes of social relations in Africa and facilitated the modernization of fraudulent practices (International Journal of Cyber Criminology, 2008). In 2012, Trend Micro predicted that a cybercriminal underground market would emerge from the West African region. This prediction was reiterated by Trend Micro and INTERPOL in 2017.
One of the best and most recent reports on this growing threat is Raffile, P, et al (2024), A Digital Pandemic: Uncovering the Role of Yahoo Boys in the Surge of Social Media-Enabled Financial Sextortion Targeting Minors, Network Contagion Research Institute (NCRI). Some of the key takeaways of the NCRI report hold that financial sextortion is the most rapidly growing crime targeting children in the United States, Canada, and Australia (up 1,000% in the past 18 months) and nearly all this activity is linked to the Yahoo-boys.
The U.S. Department of Justice, National Strategy for Child Exploitation Prevention and Interdiction, A Report to Congress – 2023, provides good historical context on this growing public health crisis:
- Scale: Today, there are more victims and more offenders than ever before, and a seemingly endless stream of child sexual abuse material (CSAM) circulating online
- Complexity: The advent of so many different online platforms with global reach, the proliferation of encryption and anonymizing technology, and the ubiquity and acceptance of the co-mingling of adult and child users, have complicated the identification, interdiction, and investigation of online child sexual exploitation (OCSE)
- Dangerousness: There are younger victims (trickle down from older siblings) and increasing incidents of depression, anxiety, post-traumatic stress disorder (PTSD) and self-harm, including suicide
On 7 Feb 2023, the Federal Bureau of Investigation (FBI) and its international law enforcement partners issued a joint warning about a global financial sextortion crisis. On 5 Dec 2023, the Director, FBI, testified before the U.S. Senate Committee on the Judiciary about the explosion in incidents of children and teens being coerced into sending explicit images online and extorted for money. In 2022, law enforcement received over 13,000 reports of this type of crime, resulting in at least 12,600 victims here and abroad, and more than 20 suicides. These numbers are likely significantly underreported since research shows many victims remain silent out of feelings of embarrassment, fear, helplessness, isolation, panic, self-blame, shame, and/or shock (Thorn, 2017).
At the time of this writing, the NCMEC CyberTipline (began tracking sextortion in 2013) received 186,819 reports in 2023 of online enticement, the category that includes sextortion. In this category, there were 19,174 reports in 2019; 37,872 in 2020; 44,155 in 2021; and 80,524 in 2022 (NCMEC, 2023).
Examples of sextortion scams are available from cybersecurity firms such as Bleeping Computer, KnowBe4, Palo Alto Networks, Security Boulevard, Sophos, Trend Micro, etc. The Better Business Bureau maintains a scamtracker database with 77 results for sextortion. The above referenced NCRI report includes several examples. Court records are another good source, e.g. the indictment on three Nigerian members of a global sextortion operation that targeted more than 100 victims and led to the death of a 17-year-old boy (Case 2:22-cr-00025-RJJ, 2022).
Criminality
States with sextortion laws, https://cybercivilrights.org/sextortion-laws/
While there is no sextortion law per se at the federal level, it is considered a form of coercion and child sexual exploitation which, depending on the circumstances, may violate several federal criminal statutes, e.g., production of child sexual abuse material (CSAM) [in violation of Title 18 U.S.C. § 2251(a)], coercion/enticement of a minor [in violation of Title 18 U.S.C. § 2422(b)], receipt/possession/ distribution of CSAM (in violation of Title 18 U.S.C. § 2252A), and/or extortion via interstate communications [in violation of Title 18 U.S.C. § 875(d)] (FBI I-060523-PSA, 2023). Nearly every state has laws criminalizing the nonconsensual dissemination of intimate images (NDII) under revenge pornography or sexting laws and a dozen states have criminalized the act of sextortion (Cyber Civil Rights Initiative, 2023).
The Primary Threat Actor
Yahoo-boys is a term which emerged in the 1990s when the Nigerian prince con men transitioned to cyber/internet fraud (Yahoo-Yahoo, wire-wire, waya-waya, G-work) with the dawn of the Internet. The Yahoo-boys term stemmed from the groups’ reliance on Yahoo email and Messenger services to conduct their fraud. Yahoo-boys are also known by other terms such as Yahoo Boys, Yahoo Yahoo Boys, Yahoo Boyz, Yahooze, 419 (a reference to a section of the Nigerian criminal code pertaining to fraud), Sakawa Boys (Ghana), Gee boys (Ghana), etc.
These distributed groups are primarily based in West African countries and South Africa for many reasons: corruption, bribery and abuse of office, poverty, unemployment and lack of career opportunities, lack of an institutional framework to fight cybercrime, moral and societal acceptance of scamming, materialism, etc. However, scammers can operate from anywhere in the world, and their tactics and techniques continue to evolve.
Flores, R, Yamazaki, T, et al (2017), Cybercrime in West Africa: Poised for an Underground Market, Trend Micro and INTERPOL, describes two major types of cybercriminals acting in West Africa – Yahoo-boys and next level cybercriminals also known as SilverTerrier (Palo Alto Networks Unit 42), Wire-Wire Group 1 (WWG1), or Threat Group-2798 (TG-2798) (Secureworks). The Yahoo-boys excel in committing simple types of internet fraud (sextortion, advance-fee, stranded-traveler and romance [Catfishing] scams/fraud) under the supervision of ringleaders or masterminds. Next-level cybercriminals, meanwhile, are more experienced and prefer to pull off “long cons” (business email compromise [BEC] and tax scams/fraud) or crimes that require more time, resources, and effort. They use malware (keyloggers, remote access tools/Trojans [RATs], etc) and other crime-enabling software (email-automation and phishing tools, crypters, etc) that are easily obtainable from underground markets.
The following attributes are often associated with Yahoo-boys conducting low-level scams:
- Middle class males who are expected to work but cannot due to rampant unemployment
- Undergraduates or former undergraduates, college-age to late twenties
- Listen to loud music loud and wear expensive and the latest clothes and jewelry
- They spend lavishly, love material things, frequent nightclubs, and show cash and fancy cars on social media
- Brag, sag, do things loudly
- Collaborate with security agents, bank officials, etc
- Maintain local and international networks (open and underground)
- Move in groups of 2-4 when going to eateries
- Speak in Nigerian Pidgin, regional slang, or use coded languages with words such as “Mugun,” “Maga,” and “Maga don pay,” which all mean “the fool (i.e., their victim) has paid”
- Use “juju” (voodoo) charms (Yahoo Plus, Yahoo Plus Plus) for spiritual protection and to charm potential victims to improve their success
- Evil intentions stemming from neurotic, pathological liars who scam because they enjoy the power and ego trip. They are immensely insecure and have no sense of self-worth other than what they feel when they successfully deceive another. They take pleasure in knowing they cause others pain. They excuse and justify themselves with claims of retribution for past social injustices, i.e., slavery, etc (Cyberpsychology, Behavior, and Social Networking, 2011; Romance Scam, 2013).
Tools, Techniques, and Processes
This article is the second part of a two-part series on the recent upsurge in sextortion. Part 1 detailed the nature and scope of the threat, applicable criminal statutes, and background on the primary threat actor – distributed groups of the Yahoo-boys. Part 2 summarizes their methods and tools being used to conduct sextortion-at-scale, victim traits targeted by cybercriminals, and protective/preventative measures.
Developing a sextortion attack capability is neither expensive nor time-consuming. It requires relatively little technical skill and does not require the actual compromise of the target’s computer. Cybercriminals’ mix of tools and techniques can change, as required, so their capability inventory is almost limitless.
There are several excellent resources that detail the Yahoo-boy’s mode of operation, commonly used schemes/formats, methods of funds transfer, strategic collaborations, the continuity of operations, as well as strategies to evade tracking and arrests by security agents (NCRI, 2024; Journal of Academics Stand Against Poverty, 2023; Secureworks, 2016; KrebsOnSecurity, 2013; etc). The Yahoo-boys openly share their sextortion tools and methods by advertising their services or offering training courses via social media (TikTok, YouTube, Scribd, Facebook, etc), sharing templates of messages to victims and examples of fake social media personas they can replicate. Many of the email addresses and telephone numbers targeted by the scam and the passwords sent as proof to the victims are collected from published usernames and passwords from old website breaches, data aggregators, and/or people databases, all widely available on the Internet.
27 Feb 2024
Paul Raffile
Last month, I said it would only be a matter of time until another kid kills himself from this scam. Well, SEVEN more kids have been confirmed dead since then.
⚠️ This is a public safety emergency. It’s called financial sextortion, and it’s surging up 7200% according to NCMEC.
Here’s what parents need to know:
– Almost all of the financial sextortion targeting minors is coming from a loosely affiliated group of cybercriminals called the “Yahoo Boys” located in Nigeria and Ivory Coast.
– Almost all of the financial sextortion targeting minors is occurring on Instagram and Snapchat.
– Criminals are using catfish accounts to send hundreds of thousands of follow requests to boys on Instagram, every day, impersonating young females. The moment the teen accepts, the criminal takes screenshots of his Follower and Following lists.
– Then, the criminals lure the kids to Snap, where they coerce the kid to send an explicit photo. Boom. Now, the relentless blackmail starts. “I have your nudes and everything needed to ruin your life… I will send this to all your followers, unless you pay me $300 right now.”
– Yes, of course, tell your kids not to send photos like this. But the more important part of that conversation is “if it does happen, let me know, and we’ll fix it together.”
Here’s what kids need to know:
– Criminals can send what appear to be “live” photos and videos on Snapchat with the Red and Purple icons, but are actually pre-recorded videos. The catfishes are more convincing than ever.
– Criminals can screenshot and save Snapchat videos, bypassing the notification that typically alerts users when a screenshot has been taken.
– The moment an Instagram user accepts the follow request of a scammer, their follower/following lists are compromised. This gives criminals immense leverage to use as blackmail, threatening to send the compromising photos to all friends and family.
– If it happens, do not pay. Talk to a parent/adult. Help is available.
💡💡 Instagram can mitigate a vast majority of sextortion incidents by making one simple, practical, privacy change today:
– Instagram can disrupt this crime and save lives by making minors’ followers/following lists *always* private by default.
– Currently, the instant an Instagram user accepts a scammer’s follow request, their followers/following lists are exposed to the criminals. These lists are the primary source of leverage in nearly all financial sextortion schemes targeting minors.
– Meta already allows Facebook users to keep their Friends list truly private, but it does not afford teens this same privacy setting on Instagram. Why?
To summarize, they
Create several email addresses and/or obtain many different telephone numbers to establish fake online personas and/or hack accounts to use across various websites (dating, online classifieds, etc), forums, chat rooms, social media platforms and messaging applications
Generate multiple friend/follow requests to obtain targets’ friends, followers and following lists
send victims extremely threatening, manipulative and convincing socially engineered emails and messages.
They barrage victims with incessant texts and iMessages
Growing Sophistication
African Cyberthreat Assessment Report, 2021 (Interpol, 2021)
Strategy – platforms, pg 97
now employing emerging new technologies such as generative artificial intelligence (GenAI).
Numerous videos posted to Yahoo Boy networks on TikTok and YouTube provide instruction about how to exploit AI tools to conduct sextortion and other scams, specifically how to use real-time face swapping software, voice-changers, and using pre-recorded video calls to communicate with their victims.
https://www.mcclatchydc.com/news/nation-world/national/national-security/article137299218.html
GenAI
5 ways cybercriminals are using AI
https://assets.barracuda.com/assets/docs/dms/ciso-guide-ai-cybersecurity-ebook.pdf
Meta: Facebook, Instagram, and WhatsApp are all consistently under fire as primary places for grooming, sextortion, child sexual abuse materials, sex trafficking, and a host of other crimes and ills. Meta is prioritizing new projects and products, all while pursuing increased, sweeping encryption without sufficient provisions for child online safety which will aid predators in escaping detection and accountability.
John Caulfield yes we already have seen these criminals start to use Gen AI to make their catfish accounts even more convincing. Indistinguishable from a real account. Also they’ve used Gen AI to fabricate fake nudes of victims in order to threaten them.
Ojedokun, U and Ilori, A (2021), Tools, Techniques and Underground Networks of Yahoo-Boys in Ibadan City, provides several useful insights into the Yahoo-boys. The group has been involved in online scams for decades, predominantly using email and messaging as their primary means of communication. Their activities have expanded over the years to encompass various other platforms, including social media (especially Instagram, Snapchat, and Wizz), dating websites, online classifieds, and new technologies:
A common tactic of perpetrators of sextortion is the utilization of fake profiles online to target the victims, using various websites, forums, chat rooms, social media platforms and messaging applications. The perpetrators ultimately seek to coerce their targets into performing sexual acts via webcam and/or to create and/or distribute sexual images or video recordings. The images or recordings are then used to threaten the victim. The perpetrator threatens to reveal the images or recordings to the victim’s family, friends, significant others, employers, colleagues, classmates and/or others if the victim does not provide more sexualized media content, pay the perpetrator and/or engage in some other act desired by the perpetrator.
- Phishing Scams: Yahoo-Boys often employ phishing techniques to trick individuals into revealing sensitive information. They masquerade as legitimate entities, sending deceptive emails or creating fake websites that mimic trusted organizations or financial institutions.
- Blackmail Scams: Blackmail scams typically involve the scammer sending threatening emails to random recipients, claiming knowledge of infidelity, pornography use or other potentially embarrassing personal details that would be released publicly unless a cryptocurrency payment was made. The most common type of blackmail scam is where the scammer emails hundreds or thousands of people claiming to have installed malware on their computer or phone that recorded the recipient viewing pornographic sites. They then instruct the intended victim to send cryptocurrency – usually bitcoin – to the scammer in order not to have the videos sent to their friends and family.
- Advance Fee Fraud: One of the most common tactics employed by Yahoo-boys is the infamous “419 scam” or “Nigerian Prince scam.” In this scheme, they convince victims to provide upfront fees or personal information under the pretense of a lucrative financial opportunity or inheritance.
- Romance Scams: Yahoo-boys exploit human emotions by creating fake profiles on dating websites or social media platforms. They establish an emotional connection with victims and then manipulate them into sending money or valuable gifts. Sextortion becomes a part of the scam after a victim shares intimate pictures and the fraudsters threaten to release them.
- Non-Delivery Scams: Yahoo-boys sell goods online pretending to be legitimate owners. Victims pay for the order, the delivery, for clearing border hurdles, and never receive what they ordered. This scam is also prominent in real estate fraud with scammers posting pictures of non-existing apartments and houses.
The Yahoo-boys group increasingly employs tools primarily designed for legitimate usage for the commission of cybercrime. Two major categories of operational tools are generally deployed by for crime commission and illicit cash flows:
- Tools for facilitating crime commission on the cyberspace (laptop, mobile phone, printer, Internet, virtual private network (VPN), Internet protocol (IP) log-ins, and cheque samples)
- Tools for driving illicit cash flows (Bitcoin, Blockchain, Cash App, Ethereum, Paypal, and Zelle)
Sextortion cybercriminals are “bombing” high schools, youth sports teams, and universities with fake accounts, using advanced social engineering tactics to coerce their victims into a compromising situation. Generative artificial intelligence (AI) apps are being used to create content, including text, images, audio, or video, to target victims in sextortion-at-scale operations using false identities or deepfake images, AI voice cloning, AI chatbots, etc, to initiate and sustain interactions with targets. Cybercriminals can program these conversational agents to engage in dialogue that gradually escalates in a sexual nature, encouraging and inducing targets to share (and/or reciprocate) nudes or other explicit content. Once the content is obtained, it can be weaponized to facilitate sextortion.
Another difficulty we faced in the past was in creating realistic fake voices using other people’s sounds. However, nowadays, we only need three seconds of an individual’s voice to clone it and use a text-to-speech API to generate authentic fake voices.
Yes, but: In IBM’s experiment, researchers still hit a couple of hurdles.
Sometimes there was a lag in the voice clone’s response because it needed to access both the text-to-speech APIs and the chatbot telling it what to do.
Not all voice clones are convincing.
Be smart: The report recommends anyone who finds themselves in a suspicious phone call to paraphrase and repeat what was said to verify the accuracy.
Doing this will trip up the chatbots, which still struggle to understand basic conversational cues.
It’s Friday, February 02, 2024.
AI-generated voices mimicking celebrities and politicians are making it harder for the Federal Communications Commission (FCC) to fight robocalls. FCC chair Jessica Rosenworcel wants the commission to recognize calls that use AI-generated voices as artificial, making the use of voice cloning technologies in robocalls illegal.
Under the FCC’s Telephone Consumer Protection Act (TCPA), artificial voice or recording calls to residences are against the law. If AI-generated voice calls are recognized as illegal under the existing law, it’ll give state attorneys general offices nationwide “new tools” to crack down on scammers.
An Analysis of Financial Sextortion Victim Posts Published on r/Sextortion
Victim Identification, Assessment, Development, and Recruitment
victims’ fears, insecurities, and vulnerabilities
National Strategy, Subject Matter Expert Working Group Reports, Sextortion, Crowdsourcing, Enticement, and Coercion section, Sextortion Victims, page 97The average teenage or young-adult Internet user is the very softest of cybersecurity targets. He doesn’t use strong passwords or two-step verification, as a general rule. He clicks on links when a plausible interlocutor sends them. He reuses weak passwords across multiple accounts. And he shares material easily with other teenagers whose cyberdefense practices are even laxer than his own. This is why the sextortionists thrive.
Guilt, greed,
targeting primarily the lonely and vulnerable through dating-related mobile applications and websites as well as other social media.
Protective Measures
We continue to actively hunt for the sites hosting these scams and alert mobile device makers, wallet application developers and cryptocurrency exchanges, but the scale of these scams makes it impossible to defend against all of them.
The best defense against them continues to be public education. The Cybercrime Support Network (see I Am Being Harrassed | Revenge Porn and Sextortion) offers educational material on romance scams and investment scams that can help people spot lures for pig-butchering style crime. But reaching the people most potentially vulnerable to these scams may require a more personal touch—from friends, family, and acquaintances they trust.
Profits
Although Yahoo-boys aren’t pulling in the millions-of-dollars-a-time that some ransomware gangs seem to be getting away with, sextortion scammers have nevertheless been pulling in as much as $100,000 a month simply by telling people to pay up. (SophosLabs, 2020)
Protective / Preventative Measures
App Danger Project
the website allows you to check if your email address and credentials appear on the dark web. https://exposed.lol/
Using password managers, not re-using passwords across accounts, and using services such as HaveIBeenPwned.com or Google’s Password Checkup can protect people from the use of old passwords by attackers.)
Because scammers use and re-use (with different usernames and photos) scripted fake personas, searching on these profiles may provide some indication of a scam.
RedCompass Labs, RedFlag Accelerator (RFA) infographic, How to Follow the Money of a Sextortion Victim, 23 Jan 2024, provides the following red flag indicators:
🚩 Sending Sextortion-related Payment References
🚩 Minor Sending Funds to Inexplicable Creditor
🚩 Minor Purchasing Gift Cards / Prepaid Cards
🚩 Minor Customer Activity Related to Cryptocurrency
The full version of the RFA data model is openly available to banks and other financial organizations, expert modern slavery and human trafficking (MSHT) NGOs and other key stakeholders, including law enforcement and financial intelligence units, industry associations and academic research partners who sign up via the RFA website (www.redflagaccelerator.com). While most of us are not in banking compliance roles, we should all be aware of some of the basic observable contextual indicators involved in the various forms of MSHT.
sextortion can begin in many different ways, including:
- Catfishing/Scamming: Someone sends you a message from a fake social media account. They share an intimate image of themselves (that might be stolen from someone else or created using AI) and ask you to share one back
- Grooming: Someone spends time building a friendship or relationship with you online so that you start to trust them and feel OK about sharing intimate messages and images
- Hacking: Someone claims to have hacked your device or account and found intimate images of you (they might have hacked it or they might just be saying they have hacked it)
- Revenge: A former partner who wants to reconcile or humiliate you gets in touch to say they are going to publish intimate images that you had previously sent to them or allowed them to take.
- Editing: Someone contacts you and threatens to create inappropriate images of you using digital editing tools or AI
https://www.yubo.live/blog/sextortion
Resources
Only three platforms specifically address sextortion in their transparency reports
OECD (2023), Transparency Reporting on Child Sexual Exploitation and Abuse Online, OECD Digital Economy Papers, No. 357, OECD Publishing, Paris, https://doi.org/10.1787/554ad91f-en, examines the policies and procedures of the world’s top-50 global online content-sharing services related to child sexual exploitation and abuse (CSEA) material, providing an objective factual snapshot in time of the services’ current practices, with a focus on transparency reporting. Annex B. Profiles of the Top-50 Services, addresses sextortion in the Terms of Service (ToS) or Community Guidelines/Standards for Facebook, Snapchat, and Google Drive.
Reddit’s r/Sextortion is the world’s largest sextortion support forum and provides insight into some of the methods and tactics used by cybercriminals.
Financial Crimes Enforcement Network (FinCEN) notice, “FinCEN Calls Attention to Online Child Sexual Exploitation Crimes,” FIN-2021-NTC3, 16 Sep 2021:
* Calls attention to an increase in online child sexual exploitation (OCSE)
FBI webpage, Sextortion, includes information on what kids, teens, and caregivers need to know and a link to a Public Service Announcement, Malicious Actors Manipulating Photos and Videos to Create Explicit Content and Sextortion Schemes, 5 Jun 2023.
U.S. Government Accountability Office (2022), Online Exploitation of Children: Department of Justice Leadership and Updated National Strategy Needed to Address Challenges, GAO-23-105260.
Rajwani, K, Sextortion Red Flags, provides a compilation of Follow the Money sextortion resources for the banking industry based on work by the Canadian Centre for Child Protection, the Australian Institute of Criminology, and the National Center for Missing and Exploited Children.
Reddit’s r/Sextortion community for current or former victims of sextortion or online blackmail (now has 22.2K members).
▶️ National Center on Sexual Exploitation, Dirty Dozen 2023, Snapchat — year after year, named a top spot for sextortion, sexual interactions between minors and adults, and pornography exposure:
🔻 Child sex abuse material (CSAM) sharing and sexually explicit interactions (including with adults)
🔻 Exposure to sexually explicit content, including prostitution and pornography sites
🔻 Dangerous and risky features, such as MyAI (gives teens advice that is illegal
and in contradiction to parental guidance)
🔻 Deceptive information to caregivers around safety and well-being
Note take action option https://endsexualexploitation.org/snapchat/
▶️ Financial Crimes Enforcement Network notice, FinCEN Calls Attention to Online Child Sexual Exploitation Crimes, FIN-2021-NTC3, 16 Sep 2021, highlights:
🔻 The rise in sextortion of minors (between 2017 and 2020, there was a 147 percent increase in OCSE-related SAR filings, including a 17 percent year-over-year increase in 2020)
🔻 OCSE offenders are increasingly using convertible virtual, peer-to-peer mobile applications, the darknet, and anonymization and encryption services to try to avoid detection. CVC in particular is increasingly the payment method of choice for OCSE offenders who make payments to websites that host child sexual abuse material
🔻 OCSE facilitators attempt to conceal their illicit file sharing and streaming activities by transferring funds via third-party payment processors https://www.fincen.gov/sites/default/files/shared/FinCEN%20OCSE%20Notice%20508C.pdf
▶️ Another interesting overall resource is SmartSocial’s Ultimate Guide to Sextortion, Online Enticement, Teen Sex Trafficking, & Human Trafficking https://smartsocial.com/sex-trafficking?utm_source=Smart+Social+Mailing+List&utm_campaign=e3093112bb-Tuesday+11%2F22%2F22&utm_medium=email&utm_term=0_40b34a3ccb-e3093112bb-196272030&mc_cid=e3093112bb&mc_eid=01e5a0ad97
Offenses
While there is no sextortion law per se at the federal level, it is a form of coercion and child sexual exploitation which, depending on the circumstances, may violate several federal criminal statutes, (e.g., production of child sexual abuse material (CSAM) [in violation of Title 18 U.S.C. § 2251(a)], coercion/enticement of a minor [in violation of Title 18 U.S.C. § 2422(b)], receipt/possession/ distribution of CSAM (in violation of Title 18 U.S.C. § 2252A), and/or extortion via interstate communications [in violation of Title 18 U.S.C. § 875(d)]) (FBI I-060523-PSA, 2023). Nearly every state has laws criminalizing the nonconsensual dissemination of intimate images under sexting laws and about a dozen states have criminalized the act of sextortion, most recently Alabama, in 2019 (Hg.org, 2024).
Sextortion is a form of coercion and child sexual exploitation which, depending on the circumstances, may violate several federal criminal statutes, (e.g., production of child sexual abuse material (CSAM) [in violation of Title 18 U.S.C. § 2251(a)], coercion/enticement of a minor [in violation of Title 18 U.S.C. § 2422(b)], receipt/possession/ distribution of CSAM (in violation of Title 18 U.S.C. § 2252A), and/or extortion via interstate communications [in violation of Title 18 U.S.C. § 875(d)]) (FBI I-060523-PSA, 2023).
https://www.ic3.gov/Media/Y2023/PSA230605
Literature
This Day. (2016, April 16). Nigeria loses over N127bn annually through cybercrime. Retrieved from www.thisdaylive.com/index.php/2016/04/18/cyber-security-nigeria-loses-over-n127bn-annually-through-cybercrime/
(Aderinto & Ojedokun 2017; Ibrahim 2016; Internet Crime
Complaint Centre 2014; This Day, 2016).
Yahooboyism, a term which emerged in Nigeria in the early 2000s, is locally
used to describe a criminal subculture of youths involved in cyber fraud
perpetration (Adeniran 2008; Ajayi 2019; Ojedokun 2010).
Paul RaffilePaul Raffile
• Following • Following
Intel Analyst | Investigator | Security Strategy | Digital Risk | OSINTIntel Analyst | Investigator | Security Strategy | Digital Risk | OSINT
1w • 1w •
⚠️ Every parent needs to know about this cyber crime because it’s killing kids at an alarming rate.
This is a public safety emergency. It’s called financial sextortion, and it’s surging up 7200% according to NCMEC. The FBI just issued another round of alerts across the country.
Here’s what parents need to know:
– Almost all of the financial sextortion targeting minors is coming from a cybercrime group called the Yahoo Boys located in Nigeria and Ivory Coast.
– Almost all of the financial sextortion targeting minors starts on 1 of 3 platforms: Instagram, Snapchat, and Wizz, according to NCMEC.
– Criminals are using catfish accounts to send hundreds of thousands of follow requests to boys on Instagram, impersonating young females. The moment the teen accepts, the criminal takes screenshots of the mark’s Follower and Following lists.
– Then, the criminals lure the kids to Snap, where they coerce the kid to send an explicit photo. Boom. Now, the relentless blackmail starts. “I have your nudes and everything needed to ruin your life… unless you send me $300 right now.”
Here’s what kids need to know:
– Criminals can send what appear to be “live” photos and videos on Snapchat with the Red and Purple icons, but are actually pre-recorded videos. The catfishes are more convincing than ever.
– Criminals can screenshot and save Snapchat videos, bypassing the notification that typically alerts users when a screenshot has been taken.
– The moment an Instagram user accepts the follow request of a scam account, their follower/following lists are compromised. This gives criminals immense leverage to use as blackmail, threatening to send the compromising photos to all friends and family. These lists are the primary source of leverage in nearly all financial sextortion schemes targeting minors.
– If it happens, do not pay. Talk to a parent/adult. Help is available.
💡💡ACTION: Instagram has the power to mitigate a vast majority of sextortion incidents by making one simple privacy change today: Allow users to keep their Followers and Following lists always private and make this the default setting for minors. Currently, the instant an Instagram user accepts a scammer’s follow request, their followers/following lists are exposed to the criminals. This privacy change would mitigate a vast majority of sextortion cases.
Meta allows Facebook users to keep their Friends list truly private, but it does not afford teens this same privacy setting on Instagram. Why?
***
Carson’s death was entirely preventable. I told Snap about the exact scripts and tactics that these criminals were using back in the summer. Better detection of the scam scripts and anomalous account activity, paired with in-app safety messaging or automated blocking, would have prevented this tragedy.
FBI Internet Crime Complaint Center (IC3) data sampling of 183,939 sextortion case filings and 6,341 survey respondents and case studies. Among the findings:
- 37% of victims that comply with the demands of sextortion said the threats stopped (did not stop for 63%)
https://theconversation.com/meet-the-yahoo-boys-nigerias-undergraduate-conmen-60757
The common means of collecting fraud money in Nigeria is through the banks, mostly through the Western Union money transfer. Through compromised banking staff, fraudsters use fake identity to access funds. This is because the fraudster would have used a foreign name and would not have a recognised identity card in that name. For successful execution of fraud, an insider within the bank is important: the banker facilitates payment without attracting the attention of security agencies. They also get their share of the loot.
Yahoo-boys typically operate individually or structured in small groups. Individual groups are composed of physical communes of like-minded individuals (The Conversation, 2016).
honing their know-how, skill sets, and arsenals to slowly but surely form their own community
The instability in the Nigerian banking sector may have created an uncommitted workforce. Working in an insecure establishment makes workers vulnerable. More than 2,000 bankers have lost their jobs due to economic recession in the country. A large numbers of casual workers are deployed to man key positions in the banks. This makes way for criminal opportunities.
Therefore the “yahoo-boys” find easy allies in banking staff, who are mostly youths too, because of their socioeconomic nightmare. The fear of unemployment has been identified as a push factor for undergraduates’ involvement in internet fraud.
Romance scams are just one in the Yahoo Yahoo mix and do not rake in as much. Some others include identity theft, credit card fraud, government benefits, business/personal loans, and tax fraud.
Ironically, cybersecurity companies themselves are sometimes scammed via “callback phishing campaigns” where cybercriminals impersonate the company – and other prominent security vendors – via email to trick victims into calling them to download malware (Tech Monitor, 2022).
In 2014, Palo Alto Labs released a report that documented one of the first known cases of Nigerian cybercriminals using malware for financial gain. In 2015, FireEye also reported on Nigerian cybercriminals’ use of malware as a component of their fraud scams.
Use of Convertible Virtual Currency (CVC)
The U.S. Department of the Treasury’s Financial Crimes Enforcement Network (FinCEN) issued a Financial Trend Analysis (FTA) an increase in Bank Secrecy Act (BSA) reporting associated with the use of CVC and OCSE and human trafficking. This FTA is based on BSA reporting filed between January 2020 and December 2021.
This Financial Trend Analysis focuses on online child sexual exploitation (OCSE) and human
trafficking patterns and trend information identified in Bank Secrecy Act (BSA) data involving the
use of convertible virtual currency (CVC).
FinCEN’s analysis highlights the value of BSA reporting filed by regulated financial institutions. Key findings in the FTA include:
The total number of OCSE- and human trafficking-related BSA reports involving CVC increased from 336 in 2020 to 1,975 in 2021.
BSA filers specifically reported child sexual abuse material (CSAM) or human trafficking and CSAM in 95 percent of the OCSE- and human trafficking-related BSA reports involving CVC.
BSA reports overwhelmingly identified bitcoin as the primary CVC used for purported OCSE- and human trafficking-related activity, however, this does not necessarily mean that other types of CVC are not used for such crimes.
FinCEN identified four typologies (i.e. the use of darknet marketplaces that distribute CSAM, peer-to-peer exchanges, CVC mixers, and CVC kiosks) that describe common trends within BSA reports related to OCSE and human trafficking. (FinCEN, 2024)




